Azure Application Gateway Adfs
- Azure Application Gateway Basic
- Azure Application Gateway Adfs
- High Availability Cross-geographic AD FS Deployment In Azure With Azure Traffic Manager
We are converting a ASP.NET Web Application to Azure. The Authentication process is handled using LDAP call in the existing code, but we are planning for ADFS integration. The ADFS server already exposing the claims to Microsoft Federation Gateway to consume by other applications. Tight integration with Azure. Application Gateway is integrated with several Azure services. Azure Traffic Manager supports multiple-region redirection, automatic failover, and zero-downtime maintenance. Use Azure Virtual Machines, virtual machine scale sets, or the Web Apps feature of Azure App Service in your back-end pools. Sep 14, 2011 We are converting a ASP.NET Web Application to Azure. The Authentication process is handled using LDAP call in the existing code, but we are planning for ADFS integration. The ADFS server already exposing the claims to Microsoft Federation Gateway to consume by other applications. One of the methods I’ve used has been leveraging Azure Application Gateway (AAG) with Web Application Firewall (WAF) to protect these services. The AAG’s with WAF have been a very fast and cost effective way for clients to deploy fast and protected services to Azure without the requirement for expensive 3rd-party WAF appliance licenses.

In Part 1 of Configuring Azure Application Gateway with AD FS we covered the existing architecture AD FS and the target AD FS architecture. Finally we deployed an Application Gateway with a basic configuration. So lets have a look at the logical configuration of what AD FS with a Application Gateway running a Web Application.
Azure Active Directory's Application Proxy provides secure remote access to on-premises web applications. After a single sign-on to Azure AD, users can access both cloud and on-premises applications through an external URL or an internal application portal. For example, Application Proxy can provide remote access and single sign-on to Remote Desktop, SharePoint, Teams, Tableau, Qlik, and line of business (LOB) applications.

Azure AD Application Proxy is:
Simple to use. Users can access your on-premises applications the same way they access Microsoft 365 and other SaaS apps integrated with Azure AD. You don't need to change or update your applications to work with Application Proxy.
Secure. On-premises applications can use Azure's authorization controls and security analytics. For example, on-premises applications can use Conditional Access and two-step verification. Application Proxy doesn't require you to open inbound connections through your firewall.
Cost-effective. On-premises solutions typically require you to set up and maintain demilitarized zones (DMZs), edge servers, or other complex infrastructures. Application Proxy runs in the cloud, which makes it easy to use. To use Application Proxy, you don't need to change the network infrastructure or install additional appliances in your on-premises environment.
From the drop-down window, select 'Administrator' and select 'OK.' Or, select 'Standard user' to remove administrator rights from an account that has them. Select 'Administrator' in the pop-up. Open your 'Control Panel,' which is located on your 'Start' menu under 'Settings'. It may also be on. Remove or change administrator acccount. Jump to solution. I recently was given a Dell desktop computer from my job. Job was given computers from a local school who upgraded their computers. My situation is I can't change or modify some files or programs because I'm not the adminstrator. I don't know adminstrator password. System password recovery tool: At first, let's share one easy utility that can reset Windows. 3- Set 'Accounts: Administrator account status' to Enabled. 4- Set 'User Account Control: Admin Approval Mode for the Built-in Administrator account' to Disabled. For Windows Vista Home Basic/Home Premium: 1- Click Start, and type 'cmd' in the search area, right click on 'Command Prompt' and select 'Run as Administrator'. How to change administrator on dell laptop.
What is Application Proxy?
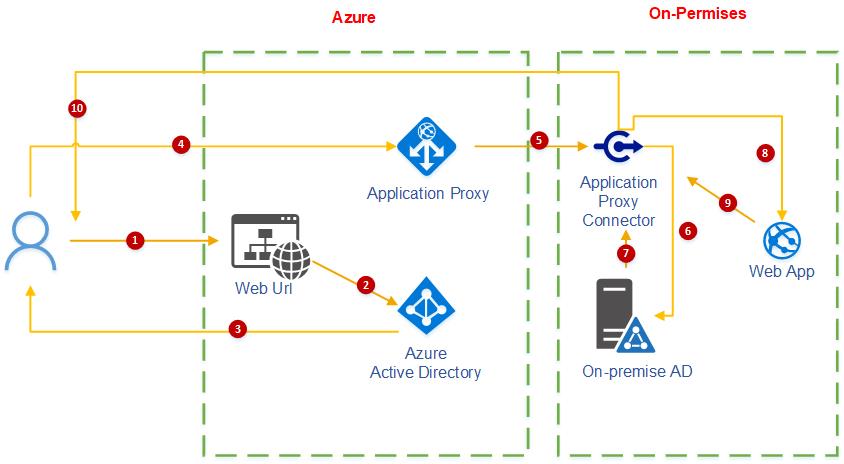
Application Proxy is a feature of Azure AD that enables users to access on-premises web applications from a remote client. Application Proxy includes both the Application Proxy service which runs in the cloud, and the Application Proxy connector which runs on an on-premises server. Azure AD, the Application Proxy service, and the Application Proxy connector work together to securely pass the user sign-on token from Azure AD to the web application.
Application Proxy works with:

- Web applications that use Integrated Windows Authentication for authentication
- Web applications that use form-based or header-based access
- Web APIs that you want to expose to rich applications on different devices
- Applications hosted behind a Remote Desktop Gateway
- Rich client apps that are integrated with the Microsoft Authentication Library (MSAL)
Application Proxy supports single sign-on. For more information on supported methods, see Choosing a single sign-on method.
Application Proxy is recommended for giving remote users access to internal resources. Application Proxy replaces the need for a VPN or reverse proxy. It is not intended for internal users on the corporate network. These users who unnecessarily use Application Proxy can introduce unexpected and undesirable performance issues.
Azure Application Gateway Basic
How Application Proxy works
The following diagram shows how Azure AD and Application Proxy work together to provide single sign-on to on-premises applications.
- After the user has accessed the application through an endpoint, the user is directed to the Azure AD sign-in page.
- After a successful sign-in, Azure AD sends a token to the user's client device.
- The client sends the token to the Application Proxy service, which retrieves the user principal name (UPN) and security principal name (SPN) from the token. Application Proxy then sends the request to the Application Proxy connector.
- If you have configured single sign-on, the connector performs any additional authentication required on behalf of the user.
- The connector sends the request to the on-premises application.
- The response is sent through the connector and Application Proxy service to the user.
Azure Application Gateway Adfs
Heidelberg sorm machine manual. Note
Like most Azure AD hybrid agents, the Application Proxy Connector doesn't require you to open inbound connections through your firewall. User traffic in step 3 terminates at the Application Proxy Service (in Azure AD). The Application Proxy Connector (on-premises) is responsible for the rest of the communication.
| Component | Description |
|---|---|
| Endpoint | The endpoint is a URL or an end-user portal. Users can reach applications while outside of your network by accessing an external URL. Users within your network can access the application through a URL or an end-user portal. When users go to one of these endpoints, they authenticate in Azure AD and then are routed through the connector to the on-premises application. |
| Azure AD | Azure AD performs the authentication using the tenant directory stored in the cloud. |
| Application Proxy service | This Application Proxy service runs in the cloud as part of Azure AD. It passes the sign-on token from the user to the Application Proxy Connector. Application Proxy forwards any accessible headers on the request and sets the headers as per its protocol, to the client IP address. If the incoming request to the proxy already has that header, the client IP address is added to the end of the comma separated list that is the value of the header. |
| Application Proxy Connector | The connector is a lightweight agent that runs on a Windows Server inside your network. The connector manages communication between the Application Proxy service in the cloud and the on-premises application. The connector only uses outbound connections, so you don't have to open any inbound ports or put anything in the DMZ. The connectors are stateless and pull information from the cloud as necessary. For more information about connectors, like how they load-balance and authenticate, see Understand Azure AD Application Proxy connectors. |
| Active Directory (AD) | Active Directory runs on-premises to perform authentication for domain accounts. When single sign-on is configured, the connector communicates with AD to perform any additional authentication required. |
| On-premises application | Finally, the user is able to access an on-premises application. |
Next steps
High Availability Cross-geographic AD FS Deployment In Azure With Azure Traffic Manager
To start using Application Proxy, see Tutorial: Add an on-premises application for remote access through Application Proxy.